During an investigation into the notorious Russian-speaking digital espionage agency Turla, Kaspersky Lab researchers have discovered how they avoided locating their activities and physical location.
To ensure anonymity, this group uses security vulnerabilities on global satellite networks.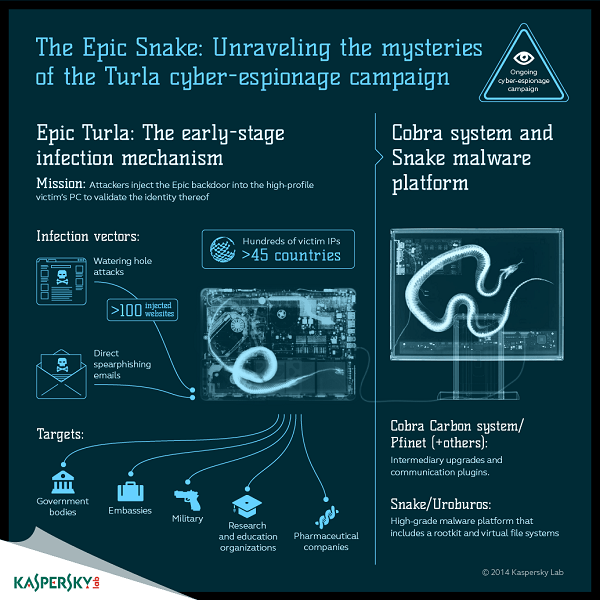
Η Turla είναι μία εξελιγμένη ομάδα ψηφιακής κατασκοπείας που είναι ενεργή πάνω από 8 χρόνια. Οι επιτιθέμενοι πίσω από την ομάδα Turla έχουν «μολύνει» εκατοντάδες υπολογιστές σε περισσότερες από 45 countries, ανάμεσα στις οποίες και το Καζακστάν, η Ρωσία, η Κίνα, το Βιετνάμ και οι Ηνωμένες Πολιτείες.
Institutions affected include government bodies and embassies, military organizations, academic and research institutions, and pharmaceutical companies. At the initial stage, the backdoor Epic develops the profile of the victims. Then - and only for higher-level targets - the attackers use an extensive satellite-based communication mechanism in later stages of the attack to help them catch up with their traces.
Satellite communications are known primarily as a tool for broadcasting television signals and for secure communications. However, they are also used to provide access to the Internetnetwork. Οι υπηρεσίες αυτές χρησιμοποιούνται κυρίως σε απομακρυσμένες περιοχές, όπου όλα τα άλλα είδη πρόσβασης στο Διαδίκτυο είτε είναι ασταθή και αργά ή δεν είναι διαθέσιμα σε όλους. Ένα από τα πιο διαδεδομένα και φθηνά είδη δορυφορικών συνδέσεων στο Διαδίκτυο είναι η λεγόμενη μονόδρομη δορυφορική σύνδεση, η οποία επιτρέπει μόνο downloading.
In this case, outgoing requests from a user's computer are communicated via conventional lines (wired or GPRS connection), with all incoming traffic originating from the satellite.
Η technology αυτή επιτρέπει στο χρήστη να έχει μια σχετικά γρήγορη ταχύτητα λήψης. Ωστόσο, διαθέτει ένα μεγάλο μειονέκτημα: το σύνολο της downstream κίνησης επιστρέφει στον υπολογιστή χωρίς κρυπτογράφηση. Κάθε αδίστακτος χρήστης που έχει στην κατοχή κατάλληλο και σχετικά φθηνό latest technology equipment and software could simply monitor the traffic and gain access to all the data that the users of those connections "download".
The Turla team exploits this vulnerability in a different way, using it to hide the location of its Command & Control (C&C) servers, which are one of the most important parts of the malicious infrastructure.
The C&C server is essentially the "headquarters" of malware running on targeted machines. Finding out the location of such a server can lead researchers to discover details about the operator behind a business.
Below is the way the Turla team avoids these risks:
- The team first "listens" to downloading the data from the satellite in order to find active IP addresses of Internet users who are online at the moment.
- It then chooses an IP address to use to mask a C&C server, without the legitimate user knowing about it.
- Machines that have been "infected" by the Turla operator are then instructed to transfer the data to the selected IP addresses of the Satellite Internet users. The data travels through conventional lines in the Satellite Internet provider's tele-services, reaching up to the satellite and, finally, by the satellite they reach users with the selected IP addresses.
Interestingly, the legitimate user whose IP address has been used by attackers to obtain data from an "infected" machine will also receive these data packets, but will hardly notice them. This is because Turla attackers assign "infected" machines to send data to ports that, in most cases, are closed by default. Thus, the legitimate user's computer will simply reject these packages, while Turla's C&C server, which keeps these ports open, will receive and process the "stolen" data.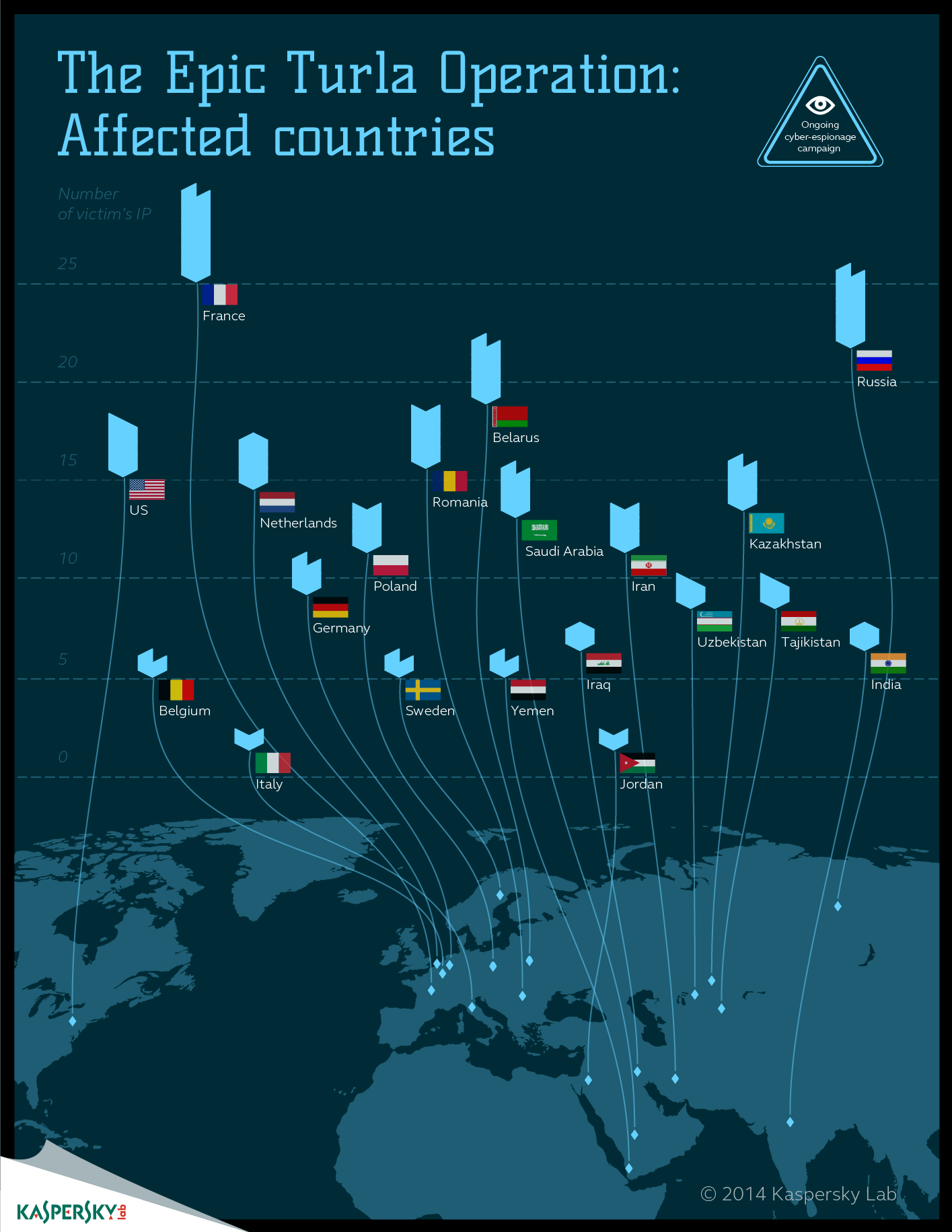
Still an interesting feature of Turla's tactics is that it tends to use Middle Eastern and African-based satellite Internet connection providers. In their research, Kaspersky Lab specialists have identified the Turla team using IP addresses of providers located in countries like Congo, Lebanon, Libya, Niger, Nigeria, Somalia or the United Arab Emirates.
Satellite beams used by providers in these countries usually do not cover areas in Europe and North America, which makes it very difficult to investigate such attacks for most security researchers.
"In the past, we have met at least three different operators using satellite links to cover their activities. Of these, the solution developed by the Turla team is the most interesting and unusual. It is able to reach the absolute level of anonymity, utilizing a widely used technology, the one-way satellite Internet. Attackers can be anywhere within the range of their chosen satellite, that is, within an area that can cover thousands of square kilometers, said Stefan Tanase, Senior Security Researcher of Kaspersky Lab. And he continued by commenting: “This makes it almost impossible to locate the intruder. Since the use of these methods is becoming more and more popular, it is important for system operators to develop sound defense strategies to mitigate attacks. "
Kaspersky Lab products detect and block the malicious software used by the threatening agent Turla under the code names: Backdoor.Win32.Turla *, Rootkit.Win32.Turla *, HEUR: Trojan.Win32.Epiccosplay.gen and HEUR: Trojan .Win32.Generic.
For more information on the abuse mechanisms of the satellite links used by the Turla espionage group, and to see the Compromise Indicators you can visit the site Securelist.com.
Watch videos and learn more about how Kaspersky Lab products can help protect against Turla's activities in a special by clicking here the company's.
Also, more information on the activities of other Russian-speaking digital espionage teams is available in another special website of Kaspersky Lab.
For more information on exploring advanced targeted attacks, you can watch one short video of Kaspersky Lab.





