Vytal is an open source extension for Chromium-based browsers that will forge location, locale, time zone, and username.
Vytal uses the chrome.debugger API, which according to this developer makes the use of the extension undetectable and thus can successfully falsify the data during the initial loading of the web pages, as well as the iframes that may exist in them.
The basic idea of Vytal is to give VPN users a tool so that they can set up location IDs so that VPNs automatically driven by them to connect can be routed according to the user's wishes. Of course, another feature of Vytal is to completely hide your real data from the websites you visit, even from VPNs.
The Vytal extension is available in the Chrome Web Store. Just visit his profile page there and install it, just like any other Chrome extension. You can check it out source code of the GitHub extension.
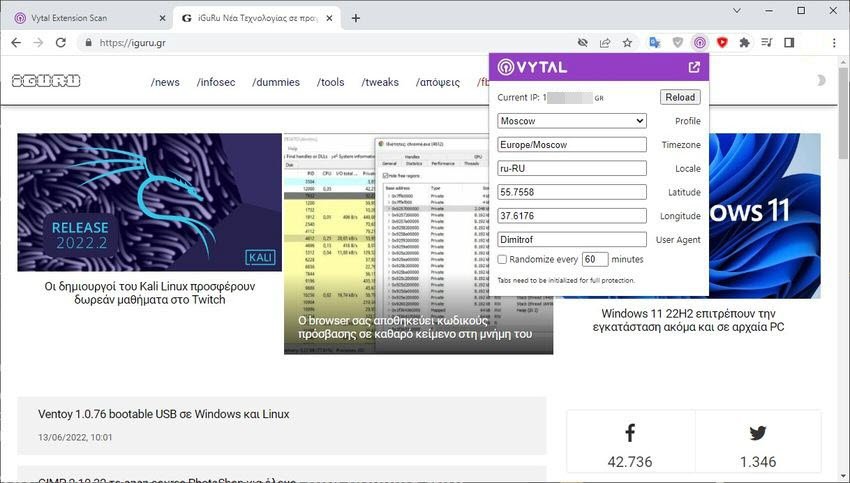
The installation adds one icon in Chrome's main toolbar that you can interact with. One click displays the available options and information about the current IP address and region.
The menu lists dozens of local location profiles that you can manually apply to spoof your location, time zone, and locale, for example the cities of Moscow, Houston, Jerusalem, or Bangkok.
A custom one is also available choice, to enter data manually in the fields, but also an option to randomize the data every 60 minutes.
Last but not least, you can also manually define a different user.
Vytal has two drawbacks that users should be aware of. Chromium-based browsers display a "Vytal started debugging in this browser" message at the top when extensions using the debugging API are enabled.
Chrome and other Chromium-based browsers support the -silent-debugger-extension-api command-line switch, which suppresses the message in the browser.
The second issue is a little more important. There is a slight delay between opening a new tab and starting the debugger. Websites may use this delay to retrieve information before the actual falsification takes place.
Because it is tab-based, users may bypass it by first loading secure sites into tabs before loading sites that may detect counterfeiting this way.
The browser extension is not available for Firefox, as the browser does not support the developer-friendly debugging API.





