WAF bypass Tool is an open source tool for analyzing the security of any WAF (Web Application Firewall) for false positives and false negatives using predefined and customizable payloads.
Check your WAF before an attacker does. WAF Bypass Tool is developed by the Nemesida WAF team with community input.
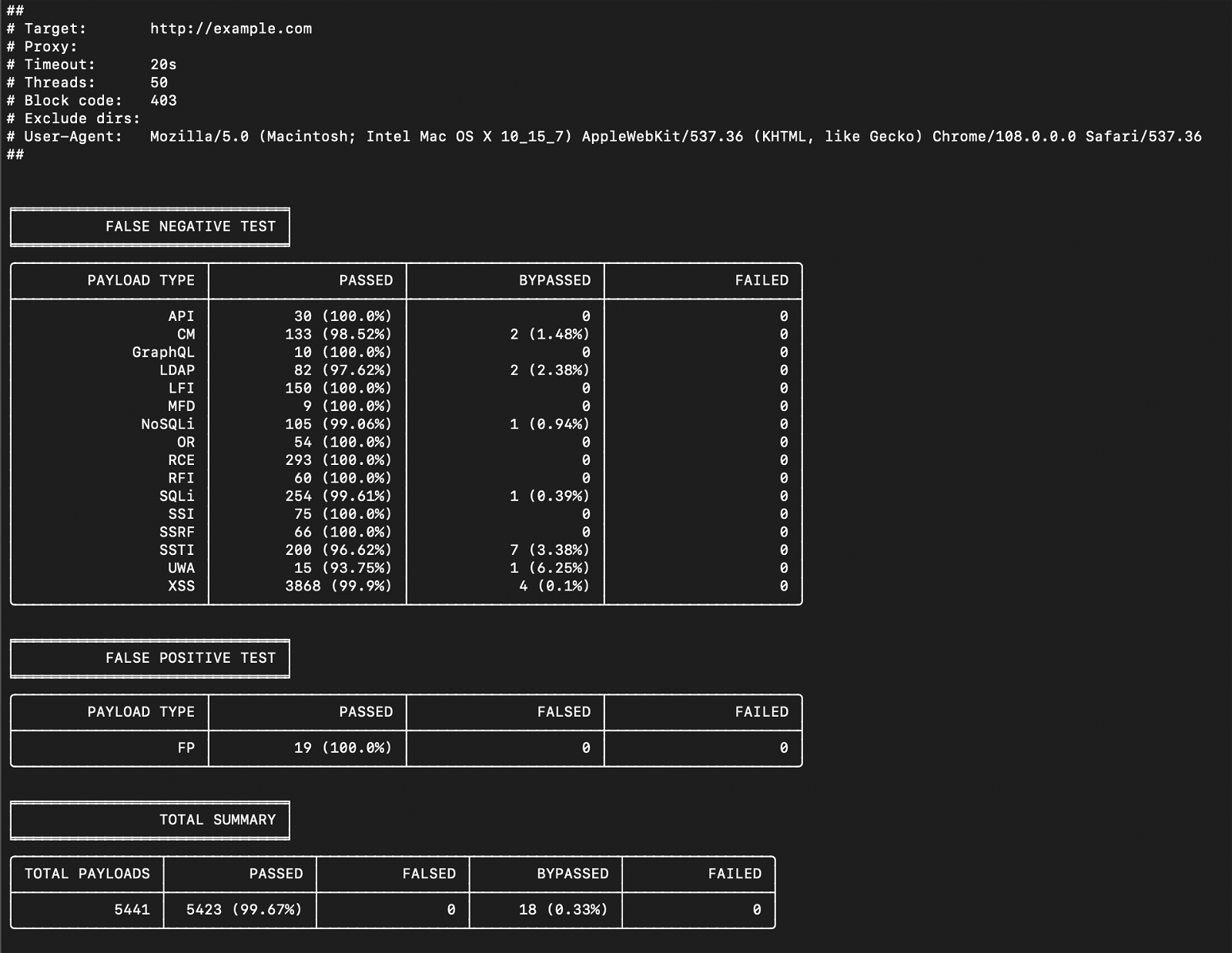
Both as a defender and as an attacker, using this tool, you can know in advance which attacks can pass the respective firewall so that no time is wasted in further testing.
Installation
Docker
# docker pull nemesida/waf-bypass # docker run nemesida/waf-bypass --host='example.com'
GitHub
# git clone https://github.com/nemesida-waf/waf_bypass.git /opt/waf-bypass/ # python3 -m pip install -r /opt/waf-bypass/requirements.txt # python3 /opt/waf-bypass/ bypass/main.py --host='example.com'
Payloads
Depending on the purpose, the payloads are located in the appropriate folders:
- FP – False Positive payloads
- API – API testing payloads
- CM – Custom HTTP Method payloads
- GraphQL – GraphQL testing payloads
- LDAP – LDAP Injection etc. payloads
- LFI – Local File Include payloads
- MFDs – multipart/form-data payloads
- NoSQLi – NoSQL injection payloads
- OR – Open Redirect payloads
- RCE – Remote Code Execution payloads
- RFI – Remote File Inclusion payloads
- SQLi – SQL injection payloads
- SSI – Server-Side Includes payloads
- SSRF – Server-side request forgery payloads
- SSTI – Server-Side Template Injection payloads
- UWA – Unwanted Access payloads
- XSS – Cross-Site Scripting payloads
Write your own payloads
When compiling a payload, the following zones, methods and options are used:
- URL – request's path
- ARGS – request's query
- BODY – request's body
- COOKIE – request's cookies
- USER-AGENT – request's user-agent
- REFER – request's referrer
- HEADER – request's header
- METHOD – request's method
- BOUNDARY – defines the contents of the application boundary. Applies only to payloads in the MFD directory.
- ENCODE – payload implementation (Base64, HTML-ENTITY, UTF-16) in addition to payload encoding. Multiple values are indicated by a space (eg Base64 UTF-16). Applies to ARGS, BODY, COOKIE and HEADER zones only. It does not apply to payloads in the API and MFD directories. Not compatible with the JSON option.
- JSON – specifies that the body of the request must be in JSON format
- BLOCKED – determines whether the request should be blocked (essay FN) or not (FP)
You can download the program from here.





