HP Wolf Security report reveals ironic 'honesty among thieves' as cybercriminals rely on dispute resolution services to ensure 'fair' transactions
HP Inc. released the HP Wolf Security report “The Evolution of Cybercrime: Why the Dark Web is Supercharging the Threat Landscape and How to Fight Back”. The findings show that cybercrime is supercharged through plug and play malware that makes it easier than ever to secure attacks. Cyber syndicates work with amateur attackers to target businesses, putting our online world at risk.
HP's Wolf Security team partnered with Forensic Pathways, a leading group of global forensics professionals, on a three-month investigation into the dark web, investigationsand analyzing more than 35 million purchases and forum posts for cybercriminals to understand how they operate, how they gain trust and how they build reputation.
Key findings include:
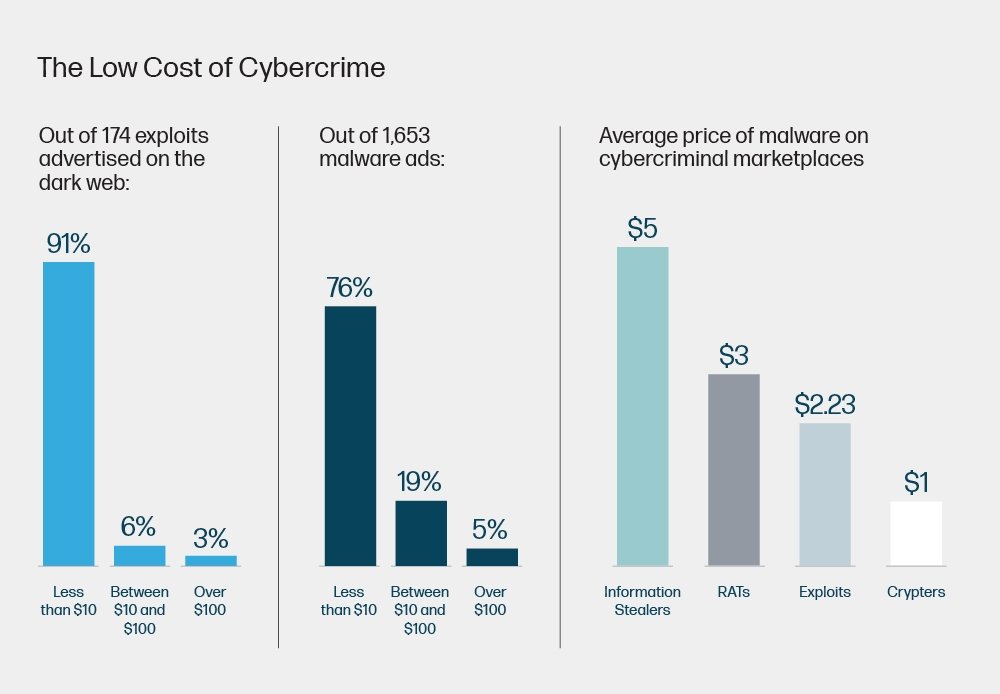
• Το κακόβουλο λογισμικό είναι φθηνό και άμεσα διαθέσιμο – Πάνω από τα τρία τέταρτα (76%) των διαφημίσεων κακόβουλου λογισμικού που αναφέρονται και το 91% των εκμεταλλεύσεων (δηλαδή κώδικας που δίνει στους εισβολείς τον έλεγχο των συστημάτων εκμεταλλευόμενοι τα σφάλματα λογισμικού), πωλούνται με τιμή λιανικής λιγότερο από 10€. Το μέσο κόστος των παραβιασμένων διαπιστευτηρίων πρωτοκόλλου απομακρυσμένης επιφάνειας εργασίας είναι μόλις 5€. Οι πωλητές πωλούν προϊόντα σε πακέτα, με κιτ κακόβουλου λογισμικού plug-and-play, malware-as-a-service, tutorials και υπηρεσίες καθdriving που μειώνουν την ανάγκη για τεχνικές δεξιότητες και εμπειρία για τη διεξαγωγή πολύπλοκων, στοχευμένων επιθέσεων – στην πραγματικότητα, μόλις 2-3% των απειλών σήμερα είναι προηγμένοι coders.
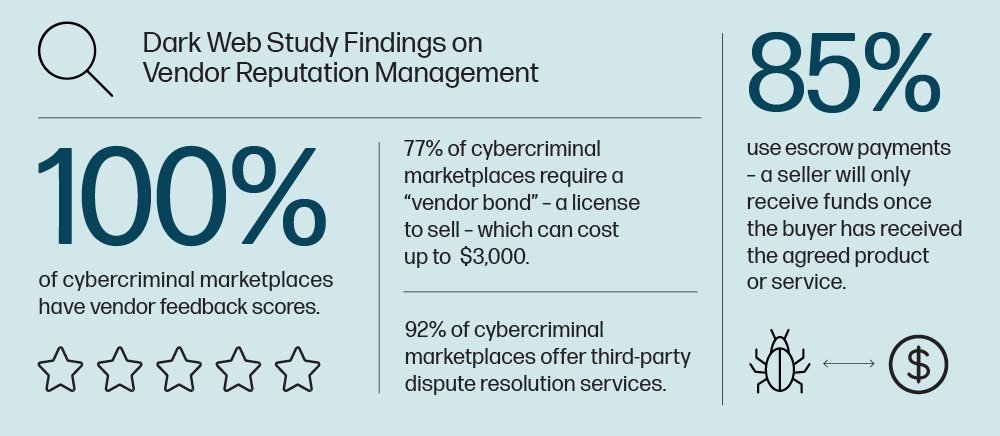
• The irony of “honesty among cyberthieves” – Like the legitimate world of online retail, trust and reputation are key parts of the cybercrime trade: 77% of cybercrime markets analyzed require a seller bond – a license to sell – something which can cost up to $3.000. 85% of them use cash guarantees and 92% have a third-party dispute resolution service. Each marketplace provides vendor feedback ratings. Cybercriminals also try to stay one step ahead of the law by transferring reputation between sites – as the average lifetime of a Tor dark net site is only 55 days.
• Popular software gives cybercriminals easier access – Cybercriminals focus on finding loopholes in software that will allow them to gain access to take control of systems by targeting known bugs and vulnerabilities in popular software. Examples include the Windows operating system, Microsoft Office, web content management systems, and web and mail servers. Kits that exploit vulnerabilities in specialized systems command the highest prices (typically ranging from $1.000 – $4.000). Zero Days (vulnerabilities not yet publicly known) sell for $10.000 on dark web markets.
“Unfortunately, it has never been easier to be a cybercriminal. Complex attacks previously required serious skills, knowledge and resources. Now technology and education are available for the price of a pack of cigarettes. And whether it's exposing your company's customer data, delaying deliveries or canceling hospital appointments, the explosion in cybercrime affects us all," said report author Alex Holland, Senior Malware Analyst at HP Inc.
HP consulted a panel of experts from cyber security and academia – including former hacker Michael 'Mafia Boy' Calce and criminology author Dr. Mike McGuire – to understand how cybercrime has evolved and what businesses can do to better protect themselves against the threats of today and tomorrow.
They warned that businesses should prepare for devastating data denial/hostage attacks, increasingly targeted cyber campaigns and cybercriminals using emerging technologies such as artificial intelligence to challenge the integrity of organizations' data.
Για την προστασία από τρέχουσες και μελλοντικές απειλές, η έκθεση παρέχει τις ακόλουθες tips για τις επιχειρήσεις:
Implement the basics to reduce cybercriminals' chances: Follow best practices such as multi-factor authentication and patch management, reduce your exposure to top attack vectors such as email, web browsing and file downloads, and prioritize in self-healing hardware to enhance resilience.
Focus on achieving the goal: Plan for the worst, limit the risk to your people and partners by implementing processes to audit supplier security and train the workforce in social engineering, be process-oriented and do attack response exercises so you can identify problems, make improvements and be better prepared.
Cybercrime is a team sport. Cybersecurity too: Talk to your partners to share threat intelligence and real-time intelligence, use threat intelligence and be proactive by monitoring open forum discussions, and work with third-party security services to discover vulnerabilities and critical risks that need addressing.
“Όλοι πρέπει να κάνουμε περισσότερα για να καταπολεμήσουμε την αυξανόμενη μηχανή του εγκλήματος στον κυβερνοχώρο”, λέει ο Δρ. Ian Pratt, Global Head of Security for Personal Systems της HP Inc. Οι περισσότερες επιθέσεις ξεκινούν με ένα click του ποντικιού, επομένως είναι πάντα σημαντικό να σκέφτεστε πριν κάνετε κλικ και το να προσφέρετε στον εαυτό σας ένα δίχτυ ασφαλείας αγοράζοντας τεχνολογία που μπορεί να μετριάσει και να ανακάμψει από τον αντίκτυπο των κακών κλικ είναι ακόμα καλύτερο”.
"For businesses, it's important to build resilience and close as many attack paths as possible," Pratt continues. "For example, cybercriminals study patches and reverse-engineer logic to reverse vulnerability and exploit the security loophole before it closes. So speeding up patch management is important. Many of the most common categories of threats, such as those delivered via email and the web, can be completely neutralized through techniques such as threat containment and isolation, significantly reducing the size of an attack on an organization, regardless of whether vulnerabilities have corrected or not".





