Comodo security software Antivirus contains too many vulnerabilities that can put them at risk users, according to researchers at Tenable Research.
Tenable Research reports that the 12.0.0.6810 version of Comodo Antivirus and Comodo Antivirus Advanced contains multiple vulnerabilities.
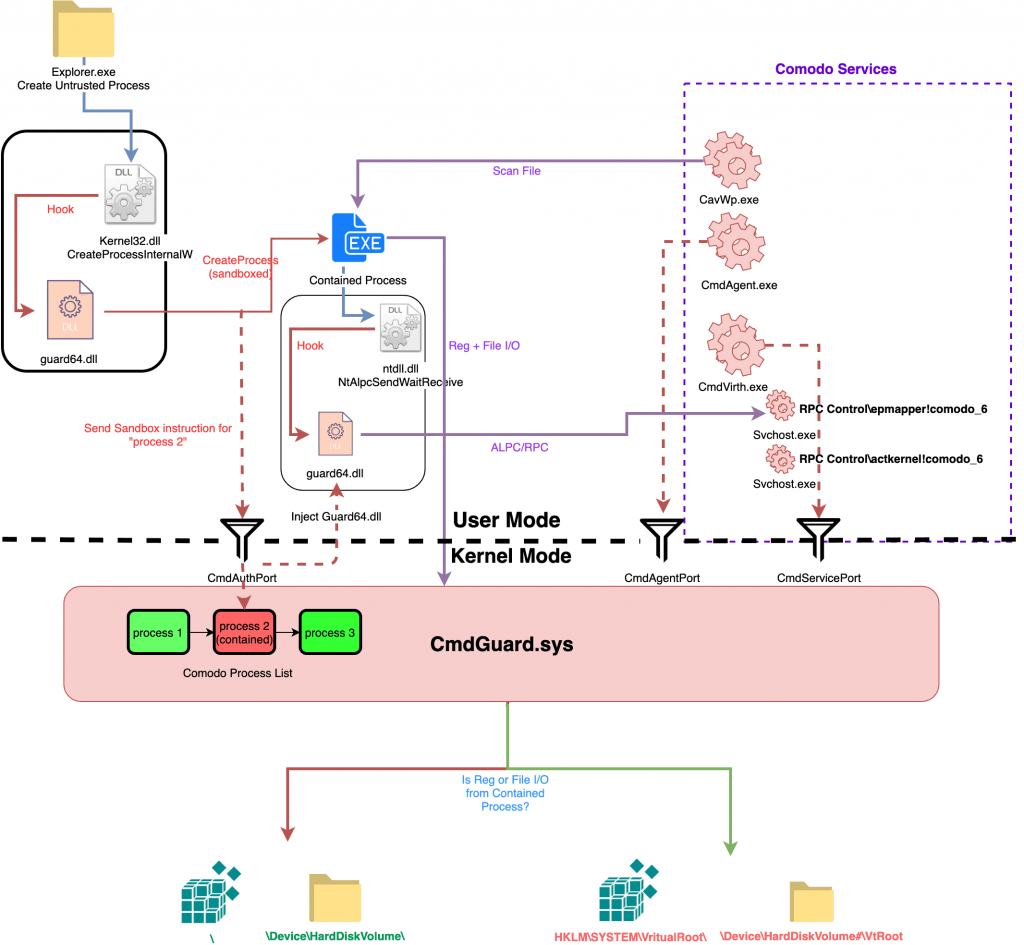
David Wells carried out an in-depth check on these vulnerabilities and in a post to Medium blog, describes how they could be used security gaps for a malicious user to escape the sandbox and gain system-level privileges. The researcher also published a PoC.
The first vulnerability, CVE-2019-3969, is a software issue in CmdAgent that allows attackers to bypass legitimate signature checks. Attackers are able to gain rights at the system level.
The second bug is CVE-2019-3970, and it appears to be a very serious one problem in handling the Comodo software database. Tenable states that the database can be stored in a protected folder on disk, but it is possible for any low-privilege process to modify the files in memory.
Another security gap is CVE-2019-3971, caused by an LCP port, cmdvrtLPCServerPort ..
Another is CVE-2019-3972, and is available at CmdAgent.exe.
The researcher also mentioned CVE-2019-3973, which affects security software only until the 11.0.0.6582 version.
Tenable's findings were reported to Comodo on April 17. By June, some of them had been confirmed, and the LPE error, according to Comodo, was "partly due to a Microsoft error."
We are currently expecting repairs from the security company. If you are using one of the applications mentioned above, it is advisable to use another, reliable one.
_________________
- Hack Right EU plan to convert black to white hat hackers
- VLC: Doubts the existence of a security vacuum
- SmartScreen disable on Windows Edge 10 1903
- Equifax 20.000 to every person who leaked his data
- Huawei: White House & Technology Companies Discuss Foreclosure
- Windows 10 May 2019 Update ISO with all the latest patches





