ESET researchers analyzed samples of malware - detected by ESET as Win32 / Industroyer - that are capable of attacking power supply infrastructures. 
There is a high probability that this particular malware is involved in the attack against the electricity network energy of Ukraines in December 2016, which led to a power outage in the country's capital, Kyiv, for an hour.
"The attack on the Ukrainian electricity grid will have to alert everyone who is responsible for the security of critical systems at the global level, warns Anton Cherepanov, Senior Malware Researcher of ESET.
ESET researchers have discovered that Industroyer can directly control electrical substation switches and circuit breakers. It uses industrial communications protocols used worldwide for power supply, transport control systems and other critical infrastructures. Possible impacts may range from a single power failure, which will result in a series of failures, even to severe damage to the equipment.
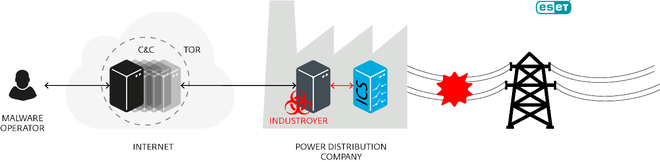
Illustration of operation of Industroyer from ESET
"Industroyer's ability to remain in the system and be able to directly interfere with the operation of industrial infrastructure makes it the most dangerous malicious threat software for industrial control systems from the famous Stuxnet", which had managed to attack Iran's nuclear program and was discovered in 2010", says Anton Cherepanov.
Detailed information about malware, as well as IOC (Indicators of Compromise) indicators, can be found in the relevant article and an extensive whitepaper on ESET's blog, WeLiveSecurity.com.





