Η ESET Research identified the BackdoorDiplomacy group, a new APT (advanced persistent threat) group that primarily targets State Departments in the Middle East and Africa, and less commonly, telecommunications companies.
Malicious attacks typically exploit vulnerable applications running on web servers to install a backdoor that ESET named Turian. The BackdoorDiplomacy team can and does detect removable storage media, most likely USB drives, and copy their contents to the recycle bin recyclingof the main drive.
The research was presented exclusively at the annual ESET World conference this week.
“The BackdoorDiplomacy team uses similar malicious tactics, techniques and procedures to those used by other groups located in Asia. The Turian is probably a further evolution of the Quarian, the malevolent software which was last used in 2013 for attacks on diplomatic targets in Syria and the United States,” says Jean-Ian Boutin, Head of Threat Research at ESET, who collaborated on this research with Adam Burgher, Senior Threat Intelligence Analyst at ESET ESET.
The protocol encryptionTurian's network is almost identical to that of Whitebird, the malware used by the Asia-based Calypso group. Whitebird targeted diplomatic organizations in Kazakhstan and Kyrgyzstan during the same time period as BackdoorDiplomacy (2017-2020).
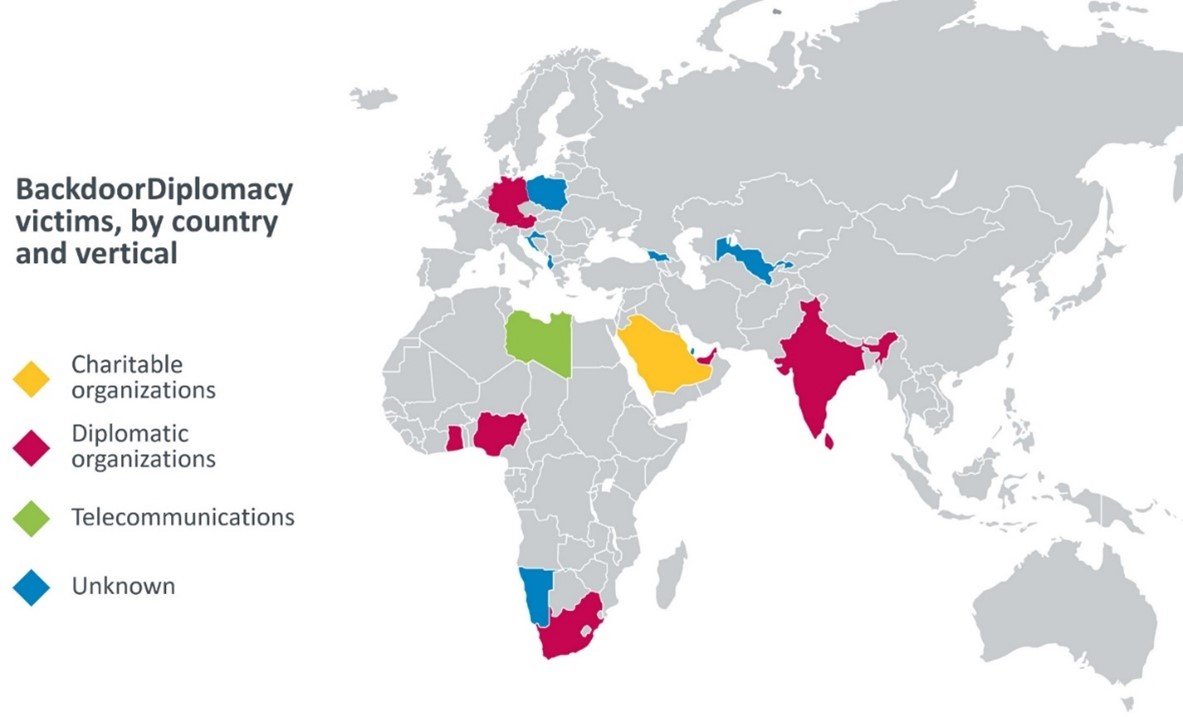
Victims of the BackdoorDiplomacy team have been identified in the Foreign Ministries of many African countries, as well as in Europe, the Middle East and Asia. Additional targets include telecommunications companies in Africa and at least one Middle Eastern charity. In any case, the cybercriminals used similar tactics, techniques and procedures, but modified the tools used, even in the same geographical areas, possibly to make tracking the team more difficult.
BackdoorDiplomacy is a team that operates on many platforms, targeting both Windows and Linux systems. The group attacks servers with ports exposed to the internet, most likely taking advantage of inadequately applied file upload security or vulnerabilities that have not been updated - in one case leading to a webshell called China Chopper and used by various groups. The cybercriminals tried to hide their traces and avoid detection.
A subset of the victims was targeted with executable data collectors, designed to search for removable media (most likely USB drives). The malware regularly scans for such drives and, when it detects removable media imports, attempts to copy all the files on them to a password file. BackdoorDiplomacy has the ability to steal the victim's system information, take screenshots and write, move or delete files.
For more technical details about the BackdoorDiplomacy team, you can read the blogpost “BackdoorDiplomacy: Upgrading from Quarian to Turian”At WeLiveSecurity.
Victims by country and by industry