Check Point Research (CPR) has identified threatening groups using documents related to the Russia / Ukraine conflict to spread malware and lure cyber espionage victims worldwide. Depending on the target and the area, attackers use official-looking documents, even news articles and job postings, as bait.

CPR believes that the motive behind these recent campaigns is cyber espionage, for the theft of sensitive information from governments, banks and energy companies. Threat groups and their victims are not concentrated in one area, but cover the whole world, including Latin America, the Middle East and Asia.
In a new publication, CPR profiles three APT groups, named El Machete, Lyceum and Sidewinder, which were recently identified conducting spear-Phishing in five countries. The table below summarizes the origin, target sector and target countries of each APT group.
| APT name | APT origin | Target Sector | Target countries |
| The Machete | Spanish speaking country | Economic, Governmental | Nicaragua, Venezuela |
| Lyceum | Islamic Republic of Iran | Energy | Israel, Saudi Arabia |
| SideWinder | Probably India | Unknown | Pakistan |
Malware features
CPR investigated the malware contained in each of the three APT teams, specifically for these cyber espionage activities. Features include:
- Keylogging: steals what you enter using the keyboard
- Credentials Collection: collects credentials stored in Chrome and Firefox browsers
- File collection: collects file information on each drive and collects filenames and file sizes, allowing specific files to be stolen
- Screenshot (Screenshot)
- Data collection from the clipboard
- Execute commands
Attack methodologies

- Spear-phishing email with text about Ukraine
- Attached Word document with article about Ukraine
- Malicious macro inside the document throws a sequence of files
- Download malware on your computer
Lyceum
- Email with content related to war crimes in Ukraine and a link to a malicious document hosted on a website
- The document executes a macro code when the document is closed
- The Exe file is stored on the computer
- The next time you restart your computer, the malware is running
SideWinder
- The victim opens the malicious document
- When opened, the document retrieves a remote template from a controlled server
- The external template downloaded is an RTF file, which exploits vulnerability CVE-2017-11882
- The malware has been installed on the victim's computer
El Machete
Machete was seen sending spear-phishing messages to financial institutions in Nicaragua, with an attached Word document entitled "Dark Plans of the Neo-Nazi Regime in Ukraine." The document contained an article written and published by Alexander Khokholikov, the Russian ambassador to Nicaragua, discussing the Russian-Ukrainian conflict from the Kremlin's perspective.

Image 1 - Bait document containing an article on the Russia-Ukraine conflict, sent by the El Machete APT to Nicaraguan financial institutions.
Lyceum
In mid-March, an Israeli energy company received an email from management inews-reporter @ protonmail [.] com με θέμα «Ρωσικά εγκλήματα πολέμου στην Ουκρανία». Το email περιείχε μερικές φωτογραφίες που ελήφθησαν από πηγές δημόσιων μέσων και περιείχε έναν σύνδεσμο προς ένα άρθρο που φιλοξενήθηκε στο news-spot[.]live domain. Ο σύνδεσμος στο email οδηγεί σε ένα έγγραφο που περιέχει το άρθρο «Οι ερευνητές συγκεντρώνουν data on possible Russian war crimes in Ukraine” published by the Guardian. The same domain hosts a few more malicious documents related to Russia as well as the Russia-Ukraine war, including a copy of a 2020 The Atlantic Council article on Russian nuclear weapons and a job posting for an “Extraction / Protective Agent” agent in Ukraine.
Image 2. Bait-email using the subject of the Russia-Ukraine conflict, sent by the Lyceum team
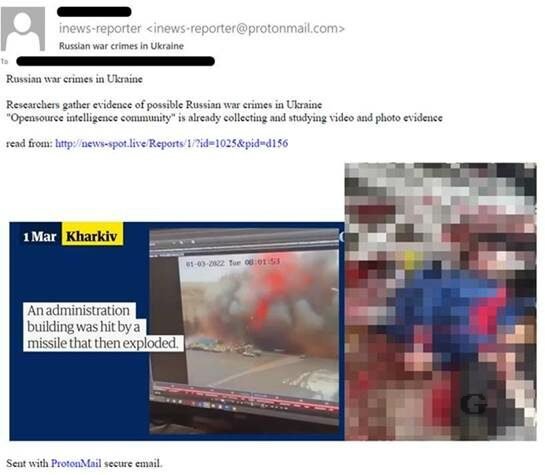
Image 3 - Bait documents related to the Russia-Ukraine war used by the APT team Lyceum

Sidewinder:
The malicious Sidewinder document, which also exploits the Russia-Ukraine war, was uploaded to VirusTotal (VT) in mid-March. Judging by its content, the desired targets are Pakistani entities. The decoy document contains a file of the National Institute of Maritime Affairs of Bahria University in Islamabad and is titled "Discussion on the impact of Russia-Ukraine conflict on Pakistan". This malicious document uses remote template injection. When opened, the document retrieves a remote template from an attacker-controlled server.
Image 4 - Bait document related to the Russia-Ukraine war, by Sidewinder APT

Comment by Sergey Shykevich, Threat Intelligence Group Manager at Check Point Software:
"Right now, we're seeing a variety of APT campaigns using the Russia-Ukraine war to distribute malware. The campaigns are highly targeted and sophisticated, focusing on government, finance and energy. In our most recent report, we profile and cite examples from three different APT groups, all from different parts of the world, that we found to orchestrate these spear-phishing campaigns. We carefully studied the malware involved and found features that cover keyboard capture, screenshots and more. I firmly believe that these campaigns are primarily motivated by cyber espionage. Our findings reveal a clear trend, that the war between Russia and Ukraine is bait used by threat groups worldwide. "I strongly urge governments, banks and energy companies to take action to raise awareness and educate their employees about cybersecurity and to implement cybersecurity solutions that protect their network at all levels."
The latest figures on cyber-attacks in Ukraine, Russia and NATO countries
Recently, Check Point Research (CPR) published an update on the trends of cyber attacks during the current Russia-Ukraine war. One month after the start of the war on February 24, 2022, both Russia and Ukraine saw increases in cyber attacks by 10% and 17% respectively.
CPR has also seen a 16% increase in cyber attacks worldwide throughout the current conflict and presents cyber attack data for countries, NATO regions and more here.





