The IoT is everywhere. From smart bulbs to IP cameras, wearables, and even smart kitchen appliances, IoT provides benefits for every organization, as it allows employees to be more productive and critical business processes to run more smoothly, intuitively and efficiently. Everywhere to such an extent that revenue from it is expected to increase to $ 549 billion in 2022 and the number of connected IoT devices is expected to reach $ 15,9 billion by 2030. (CompTIA)
However, the rush to promote this IoT technology in the market also increases the scope of cyber attacks on organizations when the security of these assets is neglected. According to Gartner, over 25% of all cyber-attacks against businesses will somehow involve the IoT.
Innovative security providers who are always thinking about the future, such as Check Point, are determined to protect users at all costs.
This article explores a real use case in which the Quantum IoT solution Protect of Check Point detected a dangerous device and protected the organization from a devastating cyber attack. But first let's quickly recap why these devices are vulnerable by design. To summarize a previous blog we published on IoT a few months ago: IoT devices often come to market with inherent flaws that make them a security risk:
- Lack of standardization creates a patchwork of devices
- Weak security approach, including weak or non-existent passwords
Outdated and unrepairable hardware, firmware or software
- Larger number of devices that widens the attack surface
As a result, it is very easy for them hackers gain access to these devices and either wreak havoc on the IoT devices themselves or move laterally to damage critical systems and steal information personally identifiable information (PII) of customers or employees, intellectual property or other assets. Hackers may also gain control of the network and hold it for ransom. And their latest trick? They combine these strategies into dual extortion attacks that promise even more lucrative returns.
How does Check Point help?
Quantum IoT Protect lets customers view all connected IoT devices on their network and monitor IoT device communications, both online and offline. This is achieved through profiles learned from understanding the expected behavior of IoT devices. Based on these profiles, customers are provided with zero-confidence access policies that allow only the communications required for normal IoT operations. Other connections are detected and blocked, for example, an attempt to connect to a suspicious Internet destination will be blocked.
So now that we have a basic understanding of how and why, here's what happened in this particular case of use.
What happened;
(Out of respect for the customer, we will keep the customer's name anonymous and refer to him as a "customer")
Quantum IoT Protect was deployed on a customer network and started detecting and identifying all connected IoT devices. Because this was the customer's first experience with IoT Protect, the customer chose to install the policies security σε λειτουργία μόνο detections, as opposed to enabling the solution to actively block suspicious traffic.
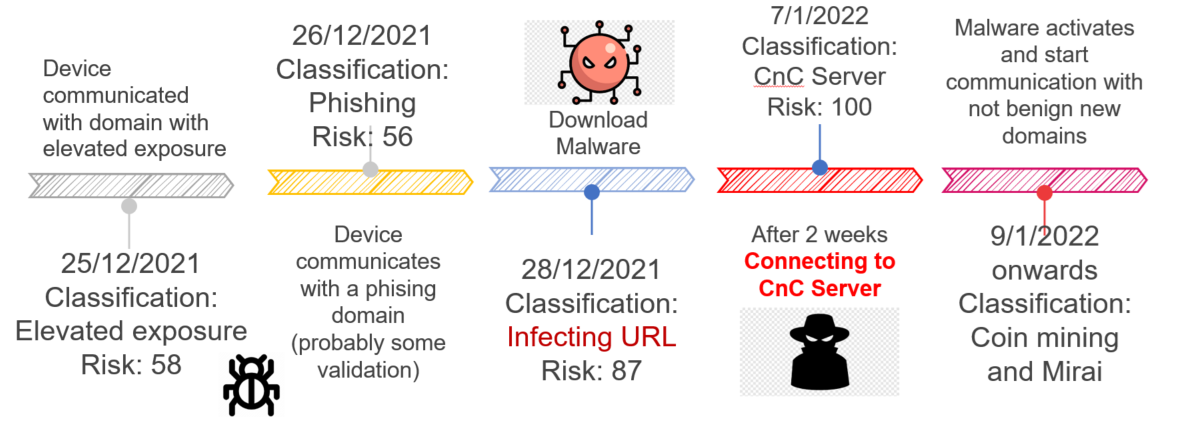
For several weeks, no suspicious activity or incident was detected until the customer saw Quantum IoT Protect detect that an IoT device was communicating with two suspicious domains for a short time. The customer then noticed that the device had stopped communicating with the suspicious domains and so decided to continue monitoring its logs.
At this point, the client chose not to take further action, believing that everything had returned to normal. This was an understandable move, as the system was virtually "silent" for a few weeks and showed no abnormal IoT device activity.
However, after two weeks of inactivity, the same device reappeared and this time began communicating with dozens of suspicious domains on the Internet. At this point the client realized that something was wrong and decided to contact the Check Point IoT team proactively for further support.
The research
At the beginning of the investigation, the Check Point team found that the device was communicating with some areas that had a high risk reputation. Further investigation of these events led to the conclusion that the device was communicating with one or more Command & Control (C&C) servers.
The response team confirmed that this IoT device was infected with Mirai and crypto mining bots. Further analysis of the logs showed exactly how the device was infected and identified the various stages of the infection and was able to describe to the customer where they were in the Cyber Kill Chain timeline.
What We Learned
At the beginning of this story, we described how the client installed Quantum IoT Protect and why it ran in scan mode only. In other words, the client had not enabled the protections that would allow him to secure the IoT devices.
The customer simply did not want to disrupt or possibly "break" the functionality of the device. This is a very common concern and is understandable. IoT devices simply do not come with well-defined instructions that indicate which connections should be allowed for normal operation and, by definition, which should not be allowed or simply blocked. Check Point addresses this legitimate concern with the Quantum IoT Protect solution.
Quantum IoT Protect provides customers with autonomous out-of-the-box zero-confidence access policies that automatically secure IoT devices without disrupting or interrupting their normal operation. To reap the true benefits of IoT devices without taking on additional security risks, customers can safely choose to deploy the Quantum IoT Protect solution in preemptive mode.
Our customer history has a happy ending - Quantum IoT Protect prevented the infected device from communicating with the servers DC and was able to clean the infected device and put it back into operation, into production.
For more information on how to start protecting your body from cyber threats, visit the Quantum IoT Protect website and schedule a IoT Security Checkup.





