Smersh is one tool specially configured for pentesters, used to track the progress of work in a company and create interactions between them.

Project architecture
SMERSH uses a lot docker containers in its architecture, which means you have to allow some services. Below you will see the full list of ports you need to open. Additionally, you will see the schema that makes up the database.

Port mapping
| Container | DefaultDNS |
|---|---|
| Api | api. {DOMAIN} |
| Bitwarden | bitwarden. {DOMAIN} |
| Client | OM DOMAIN} |
| Db | NOT EXPOSED |
| php | NOT EXPOSED |
| CodiMD | codimd. {DOMAIN} |
| db-codiMD | NOT EXPOSED |
Her life cycle applicationς
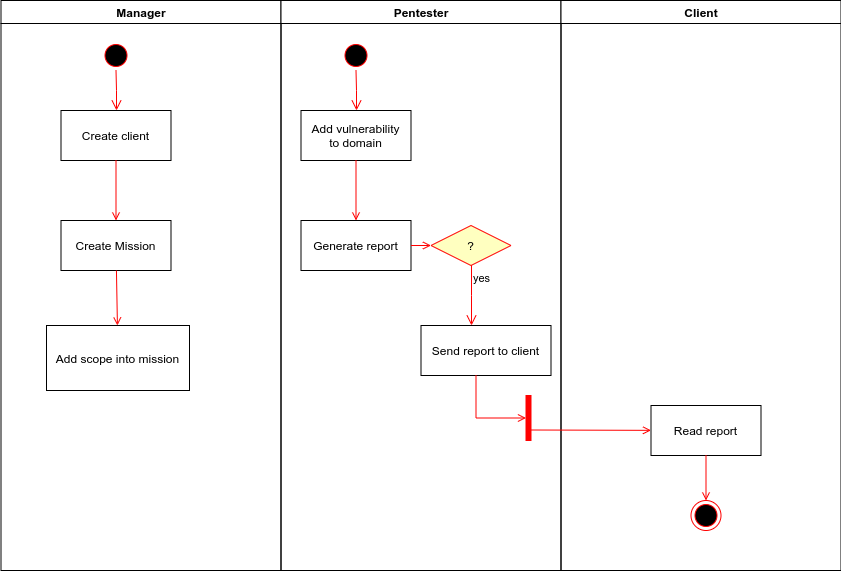
SMERSH is designed in such a way that the person in charge of each company prepares the target and all that remains is the pentester to fill in the gaps points that were detected during the control it will carry out.
Installation of the program
Information about installing the program, you will find here.





