See in this article what exactly the abbreviations represent TCP and UDP, and what are their differences.
If you are not a network engineer then it might be difficult to understand the concept of TCP and UDP. Let alone their differences.
But you have surely come across them, as for example with the inbound and outbound rules of Windows Defender, or in the port-mapping settings of your router.
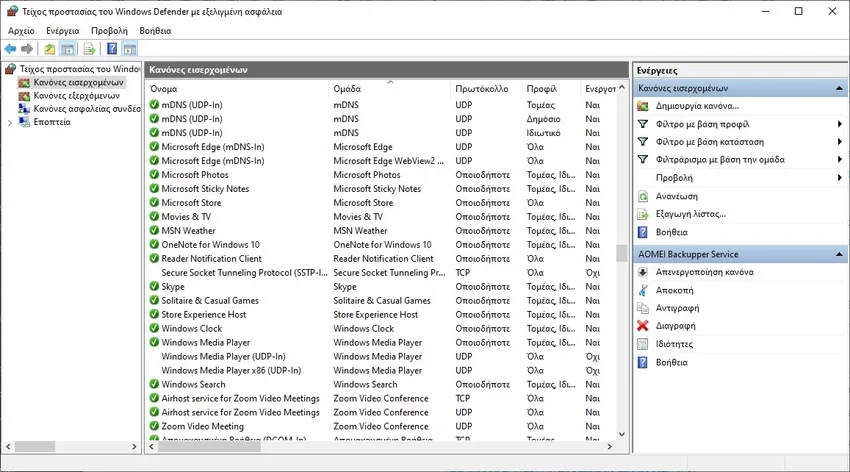
If you do a web search you will see that there are more available information over TCP rather than UDP.
But both are the most widely used data transfer protocols. Let's look at them more extensively, as well as the pros and cons of each.
What is a Protocol?

A protocol is a set of rules and guidelines that govern communication and interaction between different entities in a system (I like this definition, it reminds me of school! Please put it in the next textbook).
In the context of computer networks, a protocol defines how data is transmitted, received, and interpreted between devices or systems to enable effective communication.
Network protocols are specifically designed to facilitate the exchange of data and information between devices connected to a network. They establish standards for data formatting, error detection and correction, addressing, routing, and various other aspects of network communication.
Dive into our Greek: Don't confuse it protocol to template. Both are agreed upon rules between people, but by the term standard we refer to a set of protocols issued by a standards organization that describe a network technology. By the word standard we also mean standardization at the hardware level. The dive is over.
Protocols can operate at different layers of the network stack, with each layer responsible for a specific aspect of communication.
For example, the Internet Protocol (IP) operates at the network layer and defines the addressing scheme and routing mechanisms, while the Transmission Control Protocol (TCP) operates at the transport layer and provides reliable, connection-oriented, data delivery.
How the internet works

Small packets of data are sent between different devices around the world and can take multiple paths to reach their destination.
The whole process, from the construction of packets, sending them, receiving them and recognizing them, is governed by rules or otherwise communication protocols. And not only these, but also all the processes required for proper communication from one computer to another, such as Internet Protocol (IP), encryption, dns, etc.
More generally, we would say that the communication of the internet (or a network) is classified into layers, each of which is for specific functions. The most common model with layers it is the OSI, also known as the seven-level model and consists of the following levels:
- Physical level (cards network, cables, bus adapters etc.)
- Data link layer (ethernet protocols, 802.11, mac address, etc.)
- Network level (IPs, routers etc.)
- Transport layer (TCP, UDP, SCTP protocols etc.)
- Session level (FDX, HDX, checkpoint, termination, restart etc)
- Presentation layer (encryption, compression, MIME encoding, etc.)
- Application layer (Telnet, FTP, SMTP and http)
We are interested today in the transport layer, since this ensures the reliable and transparent transfer of data between the end systems.
It breaks down data from its upper layers into smaller chunks, provides error detection and correction, and manages end-to-end communication sessions. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) operate at this layer.
Read: How the internet works.
TCP — Transmission Control Protocol

TCP is one of the basic transport layer protocols. TCP provides reliable, connection-oriented, communication between devices over IP-based networks.
Suppose you want to download a file from a web server using TCP. Here's a step-by-step explanation of how TCP communication will happen:
1. Create a connection:
— Your browser (the client) sends a connection request to the web server.
— The web server responds by acknowledging the request and agreeing to establish a connection.
— The client acknowledges the server's response and the two establish a reliable connection with which they begin the actual data transfer.
— This triple handshake ensures synchronization and sets the initial parameters for communication.
2. Data Segmentation:
— The file you want to download is split into smaller sections or packages. Suppose the file is split into 10 packets labeled from 1 to 10.
3. Reliable delivery:
Reliability is achieved when the sender detects lost data and retransmits it. Throughout the process, TCP uses checksums to detect any errors in packet transmission. If errors are detected, TCP requests retransmission of these packets.
— The client starts sending the packets to the server.
— For each packet sent, the client waits for an acknowledgment ( ACK ) from the server.
— Upon receiving each packet, the server sends an ACK to the client to confirm successful receipt.
— If the client does not receive an ACK within a certain time frame, the server retransmits the packet.
4. Flow Control:
It is a necessary mechanism in an environment where machines of different network speeds communicate. For example, if a computer is sending data to a smartphone that is slow to process the received data, the smartphone must be able to regulate the flow of data so that it is not overwhelmed with it.
— At the beginning of each connection, the client notifies the server about the amount of data it can cache.
— The server adjusts its packet rate to match the client's available buffer space.
5. Termination of connection:
— Once all packets have been successfully received, the client and server initiate a connection termination process.
— They exchange messages to ensure the completion of the data transfer and agree to close the connection.
— The fourth handshake completes the communication.
TCP – Pros and Cons
exclusiveness: TCP establishes a dedicated connection between two specific servers to transmit data, unlike UDP which can send data from one server to multiple servers simultaneously.
Reliability: TCP ensures reliable delivery of segments, regardless of network conditions. It uses mechanisms such as confirmation, retransmission and error detection to guarantee data integrity.
Stability: TCP incorporates congestion control mechanisms to manage and prevent network congestion. The primary goal of TCP congestion control is to ensure that the network is not overwhelmed with more data than it can handle, thereby maintaining stability.
Slow start: When a TCP connection is established or reactivated after a period of inactivity, it starts with a conservative send rate. The sender gradually increases the sending rate by exponentially increasing the number of packets sent until it detects congestion or reaches a congestion window limit.
Slow process: Continuous communication between client and server makes TCP very reliable and successfully protects the data exchanged. However, the constant communication between client and server is also responsible for slow TCP data exchanges, which ultimately create an overall slower communication.
UDP — User Datagram Protocol

UDP is a simple, lightweight protocol that belongs to the transport layer. UDP has minimal error checking, making it suitable for scenarios where speed and efficiency take precedence over reliability.
Suppose you want to send a message from one device (sender) to another device (receiver) using UDP. Here's a step-by-step explanation of how UDP communication will happen:
1. Sender Preparation:
— The sender prepares the message to be sent.
— The sender determines the recipient's IP address and port number to ensure that the message reaches its intended destination.
2. Message packaging:
— The sender encapsulates the message in a UDP packet, also known as a datagram.
— The sender includes the source port number and destination port number of the receiver in the UDP header.
— The sender calculates a price checksum based on the contents of the UDP packet, which can be used by the receiver to check for transmission errors.
3. Packet transmission:
— The sender transmits the UDP packet containing the message over the network, without a handshake.
— UDP does not establish a connection before sending the packet, so it can be sent directly to the receiver without prior synchronization.
4. Receiver socket:
— The receiver listens for incoming UDP packets on its specified port.
— When the UDP packet arrives, the receiver extracts the message from the packet.
— The receiver uses the source port number to identify the sender of the message.
5. Editing messages:
— The receiver processes the message based on the requirements of its application.
— UDP does not guarantee packet delivery order or reliability, so the recipient handles any necessary debugging orlayouts at the application level.
UDP – Pros and Cons

Connectionless Communication: UDP is a connectionless protocol, meaning it does not establish a dedicated connection before transmitting data. It allows single packets (datagrams) to be sent from source to destination, without prior synchronization or negotiation.
Fast and light: UDP is designed for speed and efficiency. It works with less protocol-related processing, making it faster and more suitable for applications that require real-time data transmission, such as audio/video streaming or gamea in real time (streaming). He doesn't waste time with handshakes!
Unreliable delivery: UDP does not guarantee the delivery of packets or the order in which they were received. It does not provide acknowledgment or retransmission mechanisms for lost or damaged packets. Therefore, reliability and error checking must be handled at the application level, if required.
Datagram size limit: UDP has a maximum datagram size limit, which depends on the underlying network infrastructure. It allows applications to send a fixed size payload without fragmentation.
Which one is the best;

There is no better and worse. Each one has pros and cons and is therefore built for a purpose.
UDP is suitable for scenarios where low overhead, speed and real-time communication are critical and some packet loss is acceptable.
It is commonly used in applications such as Domain Name System (DNS) lookups, VoIP (Voice over IP) calls, video streaming, online gaming, and other situations where on-time delivery is more important than reliability.
TCP is slower but emphasizes the stability of the connection, the secure sending of data between two computers only.
It is suitable for communication with banks, for remote management applications, meetings and in general for anything you want to reach its destination safely, tolerating the slowest speed.
So the next time you want to make a change in the port-marring of your router, you won't wonder what these TCP and UDP are.
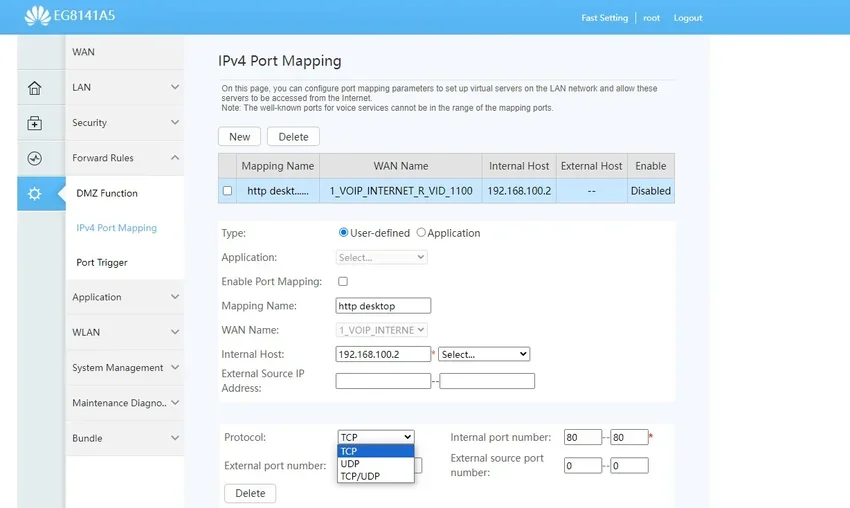
You should be able to recognize what they mean and choose the one used by the application you want to send to a computer on your network.
Like for example if you want to change port in Remote Desktop of Windows.





