Athena: WikiLeaks has released a new batch of Vault 7 leaks, which describe an eavesdropping spyware. The new CIA tool "provides capabilities to remotely connect to and load malware onto target computers," and is supposed to usesfrom the service information for every version of Microsoft's operating systems, from Windows XP to Windows 10.
Spyware is designed to be able to fully acquire full control over infected Windows computers, allowing the CIA to perform many functions on the target machine, such as data deletion or malware installation, data theft, and CIA servers.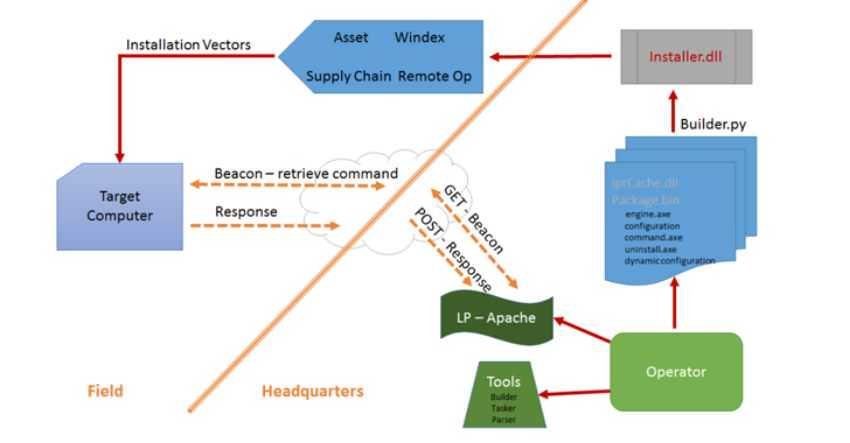
The leakage includes an Athena user manual, a technology overview, and a demonstration of how to use spyware. It reveals that malicious application can have two uses:
Lady: Athena from XP to Windows 10
Secondary: Hera for Windows 8 via Windows 10
According to WikiLeaks, Athena allows CIA agents to modify their configuration in real time, while the implant can be "adapted to a function."
“Once installed, the malware provides the ability to take pictures, configure and managementς εργασιών, φόρτωση και εκφόρτωση στη μνήμης επιβλαβών ωφέλιμων φορτίων για συγκεκριμένες εργασίες, παράδοση και recovery files from and specific folders on the target system”.
Leaked documents indicate that Athena, written in Python programming language, was developed in August of 2015, one month after Microsoft's Windows 10 operating system was released.
Interestingly, one document warns CIA agents to make sure the spyware is not exposed by programs antivirus software such as Kaspersky AV.
Athena was developed by the CIA in collaboration with Siege Technologies - an American cyber security company that offers aggressive technologies and works closely with the United States government.
However, WikiLeaks did not give any detail on Athena's activities, although it is not difficult to imagine how the CIA would use this program.
Since March, WikiLeaks has released nine leaked articles in the "Vault 7" series:
"Year Zero"The CIA is using popular hardware and software.
"Weeping Angel"The spying tool that the service uses to penetrate smart TVs, turning them into disguised microphones.
"Dark Matter"Exploits targeting iPhones and Mac.
"Marble"The source code of a secret anti-forensic framework. It's essentially a obfuscator that the CIA uses to hide the real source of malware.
"Grasshopper"A framework that allows the information service to easily create custom malicious software to violate Microsoft Windows and bypass any virus protection.
"Archimedes"- a MitM attack tool allegedly created by the CIA for targeting computers within a local area network (LAN).
Scribbles” a piece of software designed to add 'web beacons' to classified documents to allow intelligence to monitor leaks.





